
Get in Touch
Reach out to our team and discover how CERTIFY Health can revolutionize the patient’s journey for your organization.
Orange County Convention Center, Orlando, March 11-15
A digital front door system that streamlines your healthcare experience, simplifies the patient's journey, and provides easy access to the care they need.
CERTIFY'S RCM streamlines billing and collection, offering various patient-preferred payment options for more efficient transactions.
Experience faster check-ins with added security using biometric fingerprint and facial recognition, which also helps to eliminate insurance fraud.
We facilitate secure bi-directional data exchange between healthcare providers and CERTIFY platform, offering you with real-time and safe access to all patient records.
Detect coverage and prevent fraud with precision. We provide patients and healthcare providers with clarity and safety against fraudulent claims.





It’s not just Efficiency; it’s Healthcare Transformed.
We understand that every organization is unique and has its own set of processes, and we specialize in creating tailored workflow solutions designed specifically for their special needs. Whether you need simpler workflow for a small clinic or an enhanced workflow for larger institution, our platform provides user-friendly tools to create workflows that precisely fit your unique needs.
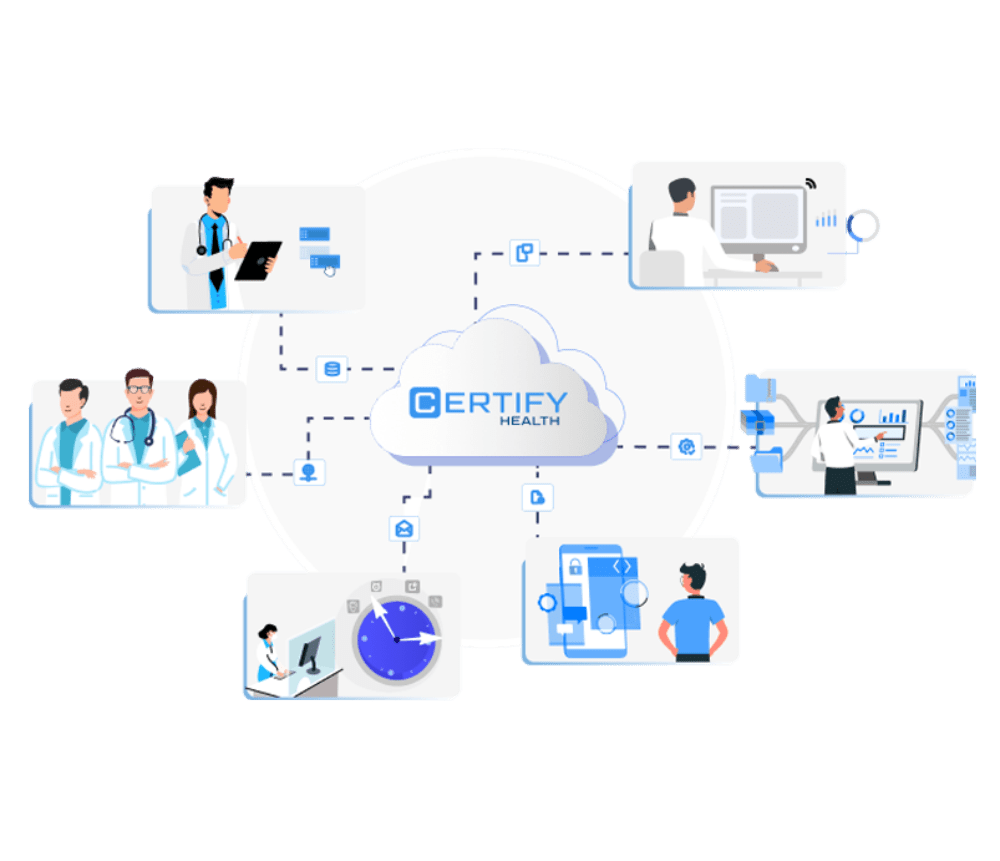
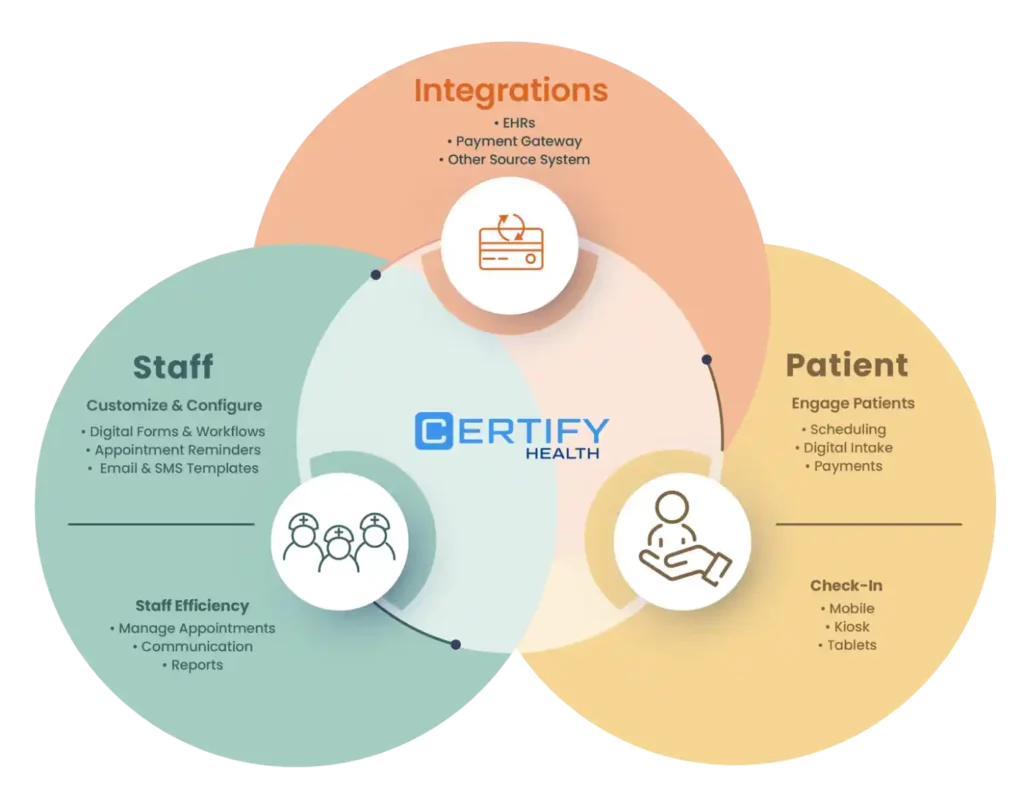


We are a leading patient engagement platform designed to improve patient experience while boosting your practice’s revenue. With CERTIFY Health, simplify your patient self-scheduling, streamline registration and intake, automate communications, and achieve financial clarity through insurance verification. Our goal is to leave every patient confident and ensure they receive the finest care possible.